Welcome to Master in Metasploit, the ultimate Android app designed for aspiring ethical hackers and security enthusiasts. Whether you're a seasoned hacker or someone eager to explore the world of ethical hacking, this app is your gateway to mastering the powerful tools of the trade.
With our comprehensive tutorials, you'll delve into the depths of Metasploit, learning how to leverage its capabilities for ethical purposes. Discover the art of exploitation and understand vulnerabilities, essential skills for any ethical hacker. From beginner basics to advanced techniques, our app guides you through every step of the process, ensuring you become proficient in the art of ethical hacking.
Learn how to use Metasploit to identify vulnerabilities and develop effective hacks while adhering to ethical guidelines. Uncover the secrets of ethical hacking as you explore real-life scenarios and interactive challenges. Whether you're interested in learning the nuances of penetration testing or enhancing your skills in cybersecurity, our app provides a rich learning experience.
Become a master in Metasploit with our user-friendly Android app. As you progress through the lessons, you'll grasp the techniques used by ethical hackers to secure systems and networks. Embrace the hacker mindset, learn the art of ethical exploitation, and elevate your knowledge in the fascinating world of cybersecurity.
This app contains the following Topics :
01. Introduction
02. What is Metasploit ?
03. Download
04. Install
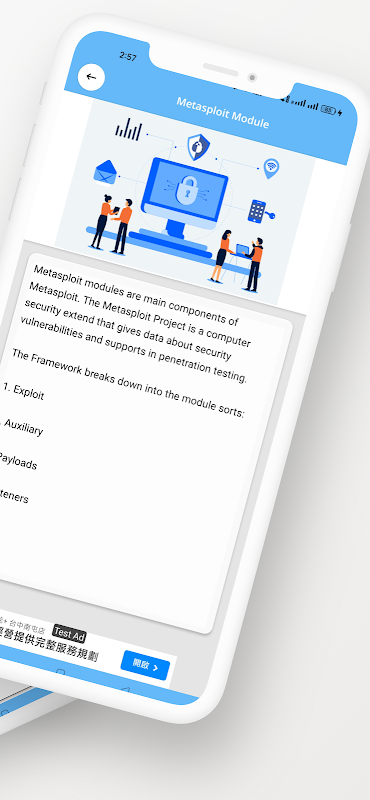
05. Metasploit Module
06. Basic Commands
07. Metasploit Meterpreter
08. Meterpreter Commands
09. Armitage
10. Reverse Engineering
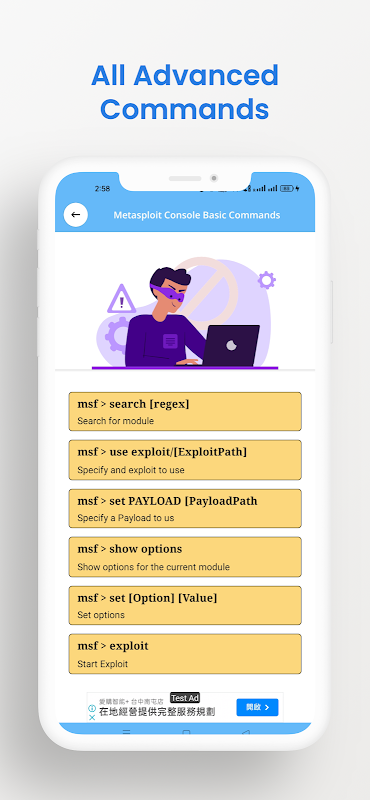
11. Metasploit Console basic Commands
12. Understand Metsploit Framework
13. Metasploit Install On ANdroid
14. Exploitation Basic
15. Exploiting Vulnerabilities
16. Scanning And Reconnaissance
17. Client Side Exploitation
18. Database Exploitation
19. Automation
20. Blue Team Exercises
21. Community And Resources
22. Evasion Techniques
23. Exploit Development
24. Payload Customisation
25. Post Exploitation Module
26. Web Application Firewall Bypass
27. Web Application Scanning
28. Payload And Shell Sessions
29. Post Exploitation Techniques
30. Social Engineering Attacks
31. Web App Penetration Testing
Download Master in Metasploit now and embark on an exciting journey of learning and exploration. Equip yourself with the skills of an ethical hacker, and unleash your potential in the realm of cybersecurity.
Metasploit is a powerful and versatile open-source framework for penetration testing and vulnerability exploitation. This guide provides a comprehensive overview of Metasploit, from its basic functionality to advanced techniques and methodologies.
Understanding Metasploit
Metasploit is a modular framework that consists of various components, including:
* Exploits: Modules that exploit vulnerabilities in target systems to gain access.
* Payloads: Code that is executed on the target system after successful exploitation.
* Auxiliary Modules: Tools for reconnaissance, information gathering, and post-exploitation tasks.
* Encoders: Techniques used to bypass antivirus and intrusion detection systems.
Basic Functionality
To use Metasploit, you must first install and configure it on your system. Once installed, you can launch the Metasploit console and begin interacting with the framework.
The basic workflow involves:
* Selecting an Exploit: Choose an exploit module that targets a specific vulnerability in the target system.
* Configuring the Exploit: Set options such as the target IP address, port, and payload.
* Launching the Exploit: Execute the exploit to attempt to gain access to the target system.
* Interacting with the Target: If successful, Metasploit will provide a session with the target system, allowing you to execute commands and perform further actions.
Advanced Techniques
Metasploit offers advanced techniques for more complex scenarios, including:
* Chaining Exploits: Combining multiple exploits to bypass security measures and gain access to highly secure systems.
* Post-Exploitation: Using Metasploit's auxiliary modules to perform tasks such as privilege escalation, password cracking, and persistence.
* Meterpreter: A powerful interactive shell that provides advanced control over the target system.
* Armitage: A graphical user interface for Metasploit that simplifies the exploitation process.
Methodologies and Best Practices
Effective use of Metasploit requires a systematic approach and adherence to best practices, such as:
* Reconnaissance: Gathering information about the target system before exploitation.
* Vulnerability Assessment: Identifying and assessing vulnerabilities that can be exploited.
* Risk Management: Evaluating the potential impact of exploitation and taking appropriate measures to mitigate risks.
* Reporting and Documentation: Properly documenting the exploitation process and results for auditing and legal purposes.
Conclusion
Mastering Metasploit empowers penetration testers and security researchers with a comprehensive toolkit for vulnerability exploitation and security assessment. By understanding its basic functionality, advanced techniques, and best practices, users can effectively leverage Metasploit to identify and mitigate security risks, enhance their security posture, and stay ahead of evolving cyber threats.
Welcome to Master in Metasploit, the ultimate Android app designed for aspiring ethical hackers and security enthusiasts. Whether you're a seasoned hacker or someone eager to explore the world of ethical hacking, this app is your gateway to mastering the powerful tools of the trade.
With our comprehensive tutorials, you'll delve into the depths of Metasploit, learning how to leverage its capabilities for ethical purposes. Discover the art of exploitation and understand vulnerabilities, essential skills for any ethical hacker. From beginner basics to advanced techniques, our app guides you through every step of the process, ensuring you become proficient in the art of ethical hacking.
Learn how to use Metasploit to identify vulnerabilities and develop effective hacks while adhering to ethical guidelines. Uncover the secrets of ethical hacking as you explore real-life scenarios and interactive challenges. Whether you're interested in learning the nuances of penetration testing or enhancing your skills in cybersecurity, our app provides a rich learning experience.
Become a master in Metasploit with our user-friendly Android app. As you progress through the lessons, you'll grasp the techniques used by ethical hackers to secure systems and networks. Embrace the hacker mindset, learn the art of ethical exploitation, and elevate your knowledge in the fascinating world of cybersecurity.
This app contains the following Topics :
01. Introduction
02. What is Metasploit ?
03. Download
04. Install
05. Metasploit Module
06. Basic Commands
07. Metasploit Meterpreter
08. Meterpreter Commands
09. Armitage
10. Reverse Engineering
11. Metasploit Console basic Commands
12. Understand Metsploit Framework
13. Metasploit Install On ANdroid
14. Exploitation Basic
15. Exploiting Vulnerabilities
16. Scanning And Reconnaissance
17. Client Side Exploitation
18. Database Exploitation
19. Automation
20. Blue Team Exercises
21. Community And Resources
22. Evasion Techniques
23. Exploit Development
24. Payload Customisation
25. Post Exploitation Module
26. Web Application Firewall Bypass
27. Web Application Scanning
28. Payload And Shell Sessions
29. Post Exploitation Techniques
30. Social Engineering Attacks
31. Web App Penetration Testing
Download Master in Metasploit now and embark on an exciting journey of learning and exploration. Equip yourself with the skills of an ethical hacker, and unleash your potential in the realm of cybersecurity.
Metasploit is a powerful and versatile open-source framework for penetration testing and vulnerability exploitation. This guide provides a comprehensive overview of Metasploit, from its basic functionality to advanced techniques and methodologies.
Understanding Metasploit
Metasploit is a modular framework that consists of various components, including:
* Exploits: Modules that exploit vulnerabilities in target systems to gain access.
* Payloads: Code that is executed on the target system after successful exploitation.
* Auxiliary Modules: Tools for reconnaissance, information gathering, and post-exploitation tasks.
* Encoders: Techniques used to bypass antivirus and intrusion detection systems.
Basic Functionality
To use Metasploit, you must first install and configure it on your system. Once installed, you can launch the Metasploit console and begin interacting with the framework.
The basic workflow involves:
* Selecting an Exploit: Choose an exploit module that targets a specific vulnerability in the target system.
* Configuring the Exploit: Set options such as the target IP address, port, and payload.
* Launching the Exploit: Execute the exploit to attempt to gain access to the target system.
* Interacting with the Target: If successful, Metasploit will provide a session with the target system, allowing you to execute commands and perform further actions.
Advanced Techniques
Metasploit offers advanced techniques for more complex scenarios, including:
* Chaining Exploits: Combining multiple exploits to bypass security measures and gain access to highly secure systems.
* Post-Exploitation: Using Metasploit's auxiliary modules to perform tasks such as privilege escalation, password cracking, and persistence.
* Meterpreter: A powerful interactive shell that provides advanced control over the target system.
* Armitage: A graphical user interface for Metasploit that simplifies the exploitation process.
Methodologies and Best Practices
Effective use of Metasploit requires a systematic approach and adherence to best practices, such as:
* Reconnaissance: Gathering information about the target system before exploitation.
* Vulnerability Assessment: Identifying and assessing vulnerabilities that can be exploited.
* Risk Management: Evaluating the potential impact of exploitation and taking appropriate measures to mitigate risks.
* Reporting and Documentation: Properly documenting the exploitation process and results for auditing and legal purposes.
Conclusion
Mastering Metasploit empowers penetration testers and security researchers with a comprehensive toolkit for vulnerability exploitation and security assessment. By understanding its basic functionality, advanced techniques, and best practices, users can effectively leverage Metasploit to identify and mitigate security risks, enhance their security posture, and stay ahead of evolving cyber threats.