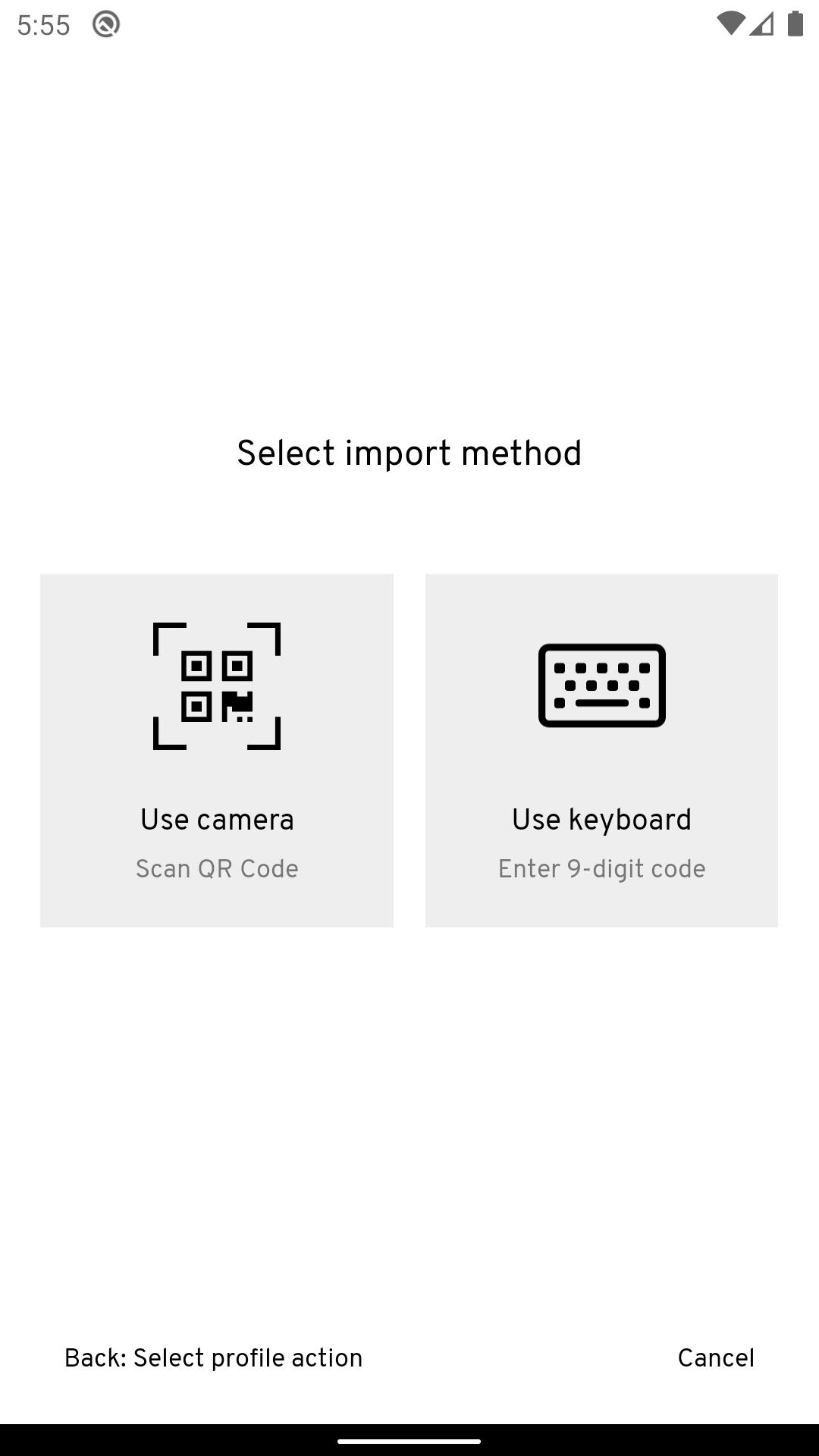
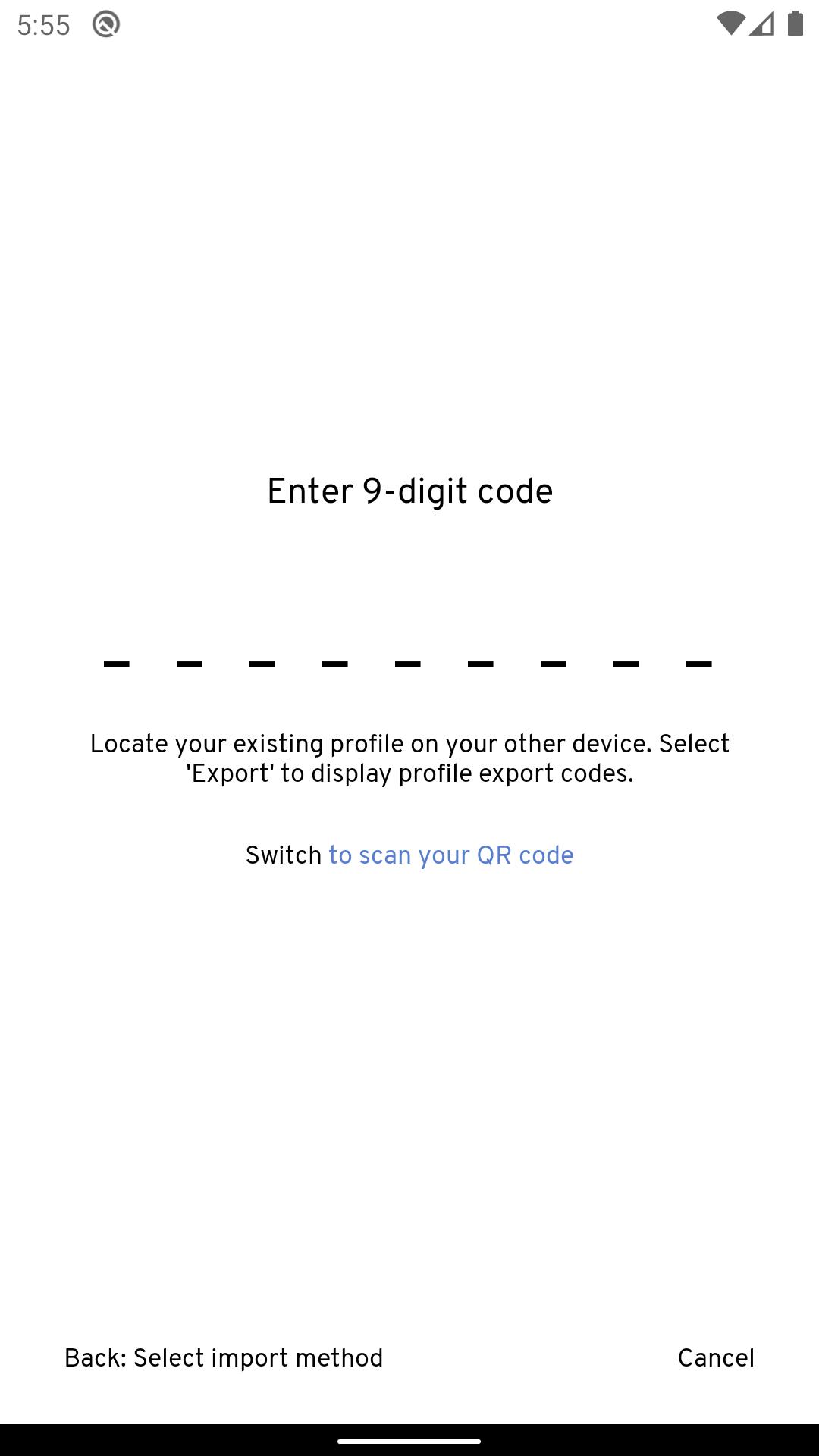
Beyond Identity's mission is to eliminate passwords in every application.
Our mission is to empower the next generation of secure digital business. By eliminating passwords and creating a fundamentally secure Chain of Trust™, our customers are able to increase business velocity, implement new business models, and reduce operating costs.
This app is intended for business use across an enterprise. If you are looking for a solution for personal use, we are working on it! Check back here for more information.
The app's usage of accessibility is only for accessing data on Beyond Identity domains during authentication and does not collect any personal or device information and does not send any personal or device information.
What's New in the Latest Version 2.98.2
Last updated on Jun 10, 2024
Minor bug fixes and improvements. Install or update to the newest version to check it out!
Beyond Identity: A Paradigm Shift in Identity ManagementBeyond Identity, a groundbreaking approach to identity management, revolutionizes the way organizations secure access to their resources. It transcends traditional methods that rely on passwords and other knowledge-based factors, embracing a more robust and secure model that focuses on verifiable attributes and continuous authentication.
Verifiable Attributes: The Foundation of Trust
Beyond Identity establishes trust by leveraging verifiable attributes that uniquely identify individuals and devices. These attributes include biometric traits, device characteristics, and behavioral patterns. By verifying multiple attributes, organizations can confidently establish the true identity of users, eliminating the vulnerabilities associated with stolen or compromised credentials.
Continuous Authentication: Monitoring for Anomalies
Beyond Identity employs continuous authentication to monitor user behavior and identify potential threats. It analyzes patterns and detects anomalies that deviate from established norms, such as unusual access times or unfamiliar devices. This proactive approach allows organizations to identify and mitigate risks in real-time, preventing unauthorized access.
Zero Trust: A Security-First Mindset
Beyond Identity aligns with the zero-trust security model, assuming that all access requests are inherently untrustworthy. It verifies every user, device, and request, regardless of location or network. This approach eliminates the concept of trusted networks and devices, ensuring that only authorized individuals gain access to sensitive data and applications.
Benefits of Beyond Identity
* Enhanced Security: Eliminates password-related vulnerabilities and provides continuous authentication for robust protection against cyber threats.
* Improved User Experience: Provides seamless and convenient access without the need for complex passwords or cumbersome authentication processes.
* Reduced Costs: Streamlines identity management processes, eliminating the need for password resets and other support tasks.
* Scalability and Flexibility: Supports a wide range of devices and applications, enabling organizations to adapt to evolving technology landscapes.
Implementation Considerations
Implementing Beyond Identity requires careful planning and execution. Organizations should consider the following:
* Phased Approach: Gradual adoption allows for testing and validation while minimizing disruption to existing systems.
* Legacy Integration: Integrate with existing identity management systems to ensure a smooth transition.
* User Education: Train users on the new authentication mechanisms and emphasize the importance of protecting verifiable attributes.
Conclusion
Beyond Identity is a transformative solution that redefines identity management. By focusing on verifiable attributes and continuous authentication, it provides organizations with unparalleled security, enhanced user experience, and reduced costs. Its alignment with the zero-trust security model ensures that only authorized individuals gain access to critical resources, safeguarding data and applications from unauthorized access.
Beyond Identity's mission is to eliminate passwords in every application.
Our mission is to empower the next generation of secure digital business. By eliminating passwords and creating a fundamentally secure Chain of Trust™, our customers are able to increase business velocity, implement new business models, and reduce operating costs.
This app is intended for business use across an enterprise. If you are looking for a solution for personal use, we are working on it! Check back here for more information.
The app's usage of accessibility is only for accessing data on Beyond Identity domains during authentication and does not collect any personal or device information and does not send any personal or device information.
What's New in the Latest Version 2.98.2
Last updated on Jun 10, 2024
Minor bug fixes and improvements. Install or update to the newest version to check it out!
Beyond Identity: A Paradigm Shift in Identity ManagementBeyond Identity, a groundbreaking approach to identity management, revolutionizes the way organizations secure access to their resources. It transcends traditional methods that rely on passwords and other knowledge-based factors, embracing a more robust and secure model that focuses on verifiable attributes and continuous authentication.
Verifiable Attributes: The Foundation of Trust
Beyond Identity establishes trust by leveraging verifiable attributes that uniquely identify individuals and devices. These attributes include biometric traits, device characteristics, and behavioral patterns. By verifying multiple attributes, organizations can confidently establish the true identity of users, eliminating the vulnerabilities associated with stolen or compromised credentials.
Continuous Authentication: Monitoring for Anomalies
Beyond Identity employs continuous authentication to monitor user behavior and identify potential threats. It analyzes patterns and detects anomalies that deviate from established norms, such as unusual access times or unfamiliar devices. This proactive approach allows organizations to identify and mitigate risks in real-time, preventing unauthorized access.
Zero Trust: A Security-First Mindset
Beyond Identity aligns with the zero-trust security model, assuming that all access requests are inherently untrustworthy. It verifies every user, device, and request, regardless of location or network. This approach eliminates the concept of trusted networks and devices, ensuring that only authorized individuals gain access to sensitive data and applications.
Benefits of Beyond Identity
* Enhanced Security: Eliminates password-related vulnerabilities and provides continuous authentication for robust protection against cyber threats.
* Improved User Experience: Provides seamless and convenient access without the need for complex passwords or cumbersome authentication processes.
* Reduced Costs: Streamlines identity management processes, eliminating the need for password resets and other support tasks.
* Scalability and Flexibility: Supports a wide range of devices and applications, enabling organizations to adapt to evolving technology landscapes.
Implementation Considerations
Implementing Beyond Identity requires careful planning and execution. Organizations should consider the following:
* Phased Approach: Gradual adoption allows for testing and validation while minimizing disruption to existing systems.
* Legacy Integration: Integrate with existing identity management systems to ensure a smooth transition.
* User Education: Train users on the new authentication mechanisms and emphasize the importance of protecting verifiable attributes.
Conclusion
Beyond Identity is a transformative solution that redefines identity management. By focusing on verifiable attributes and continuous authentication, it provides organizations with unparalleled security, enhanced user experience, and reduced costs. Its alignment with the zero-trust security model ensures that only authorized individuals gain access to critical resources, safeguarding data and applications from unauthorized access.